Originally, the most popular firewall/NAT package running on Linux was ipchains, but it had a number of shortcomings. To rectify this, the Netfilter organization decided to create a new product called iptables, giving it such improvements as:
* Better integration with the Linux kernel with the capability of loading iptables-specific kernel modules designed for improved speed and reliability.
* Stateful packet inspection. This means that the firewall keeps track of each connection passing through it and in certain cases will view the contents of data flows in an attempt to anticipate the next action of certain protocols. This is an important feature in the support of active FTP and DNS, as well as many other network services.
* Filtering packets based on a MAC address and the values of the flags in the TCP header. This is helpful in preventing attacks using malformed packets and in restricting access from locally attached servers to other networks in spite of their IP addresses.
* System logging that provides the option of adjusting the level of detail of the reporting.
* Better network address translation.
* Support for transparent integration with such Web proxy programs as Squid.
* A rate limiting feature that helps iptables block some types of denial of service (DoS) attacks.
Considered a faster and more secure alternative to ipchains, iptables has become the default firewall package installed under RedHat and Fedora Linux.
How To Start iptables?
You can start, stop, and restart iptables after booting by using the commands:
[root@bigboy tmp]# service iptables start
[root@bigboy tmp]# service iptables stop
[root@bigboy tmp]# service iptables restart
To get iptables configured to start at boot, use the chkconfig command:.
[root@bigboy tmp]# chkconfig iptables on
Determining The Status of iptables
You can determine whether iptables is running or not via the service iptables status command. Fedora Core will give a simple status message. For example
[root@bigboy tmp]# service iptables status
Firewall is stopped.
[root@bigboy tmp]#
Wednesday, November 11, 2009
What is iptables?
Monday, November 9, 2009
Understanding DNS
Understanding DNS
When you're browsing mega creations, your computer doesn't send data to www.megacreations.com It sends to 64.179.4.146. You don't have to remember the numerical address - DNS servers do it for you.
This text was written to tell you what DNS is, how it works and how you can use it. It doesn't describe configuration of your own DNS server.
Before I describe how the DNS system works, you need to know about IP adresses and domains.
IP Addresses
64.179.4.146 is an example. IP (Internet protocol) address has a form of four numbers (between 0 and 255), separated by dots. Each machine in the Internet must have an unique IP address. It works as a postal address - no message can reach the machine without a correct address.
Numbers are friendly for machines, but hard to remember for humans. That's why we have hostnames and domains (there are more reasons, for example names allow you to easily change IP addresses of servers - only the DNS entry must be changed).
Hostnames, domains, zones
An example of a hostname: www.megacreations.com It's a part of mega creations.com domain. Last portion of the address (.com) refers to a toplevel domain where the host belongs. Other toplevel domains are: .org, .net, .gov etc. Every country has its own toplevel domain. For example: .fr (France), .de (Germany), .jp (Japan) or .br (Brazilia).
Zone and domain mean nearly the same. There's one difference: zone is delegated to one server. A domain can be diveded into different zones.
How it works?
When you connect to LQ, you send a query to your DNS resolver (more about it later). The server checks if it has needed information cached. If it does, it sends it back to you. The server that stores data from previous queries is called a caching nameserver.
If it doesn't have the information you're searching for, it asks one of the root servers. Root servers are on the top of DNS servers tree (the structure looks like a tree). They contain pointers to name servers for each top level domain.
Now the toplevel domain server for .com is asked about mega creations.com domain, it knows the address of the server containing detailed information about all hosts in the mega creations.com domain.
The last server is asked about the host www.megacreations.com hosts. When your resolver server gets the reply, it sends the result back to you.
Types of DNS servers:
A caching nameserver finds answers to queries and then remembers them. This not only speeds up your response time but helps to keep the load on the root nameservers (which handle thousands of queries per second) as low as possible.
An Authoritative server is a server that can answer queries about a zone without help from any other server. Both primary and secondary servers are authoritative.
Primary server(in terms of specific zone) is a server that reads zone data from its local configuration.
Secondary server(in terms of a specific zone) gets zone data from outside sources (usually from master server).
How to use DNS servers?
The file with IP addresses of your nameservers is /etc/resolv.conf. When the machine is correctly configured, it should look like this:
nameserver 192.168.1.1
nameserver 192.168.1.3
DNS servers are listed in lines beginning with 'nameserver' (there are more things to configure in that file). In the example above there are two DNS servers: 192.168.1.1 and 192.168.1.3 (don't copy them, local addresses are used and it may not work in your network).
There's one more important file - /etc/host.conf. It should look like below:
Quote:
order hosts,bind
multi on
When the file is filled properly, everything should work fine.
Where to get the addresses from?
Your ISP is the best source. Most ISPs have their own DNS servers. They're closest to you (so should be the fastest).
If you're using DHCP (many ADSL connections) or modem, your ISP may pass the information to you when you connect. In such case, you don't need to edit /etc/resolv.conf manually.
How to test it?
You can use 'nslookup' or 'dig'.
First example, using nslookup:
sh-2.05b$ nslookup www.megacreations.com
Note: nslookup is deprecated and may be removed from future releases.
Consider using the `dig' or `host' programs instead. Run nslookup with
the `-sil[ent]' option to prevent this message from appearing.
Server: 192.168.1.1
Address: 192.168.1.1#53
Non-authoritative answer:
Name: www.megacreations.com
Address: 64.179.4.146
As you can see it gives the same answer as we got when ping was used.
Next example, using 'dig'. The command format is:
dig @DNS_server host
It returns more information, so may be harder to read. I'm asking the server 192.168.1.1 about www.linuxquestions.org. You don't need to give the DNS server. If you simply use 'dig.linuxquestions.org', your default DNS server will be used. In the 'ANSWER SECTION' you can see that www.linuxquestions.org is 64.179.4.146. In the line 'Query time' you can see how much time it takes to get an answer. In the example below the time is very short, because I use caching nameserver.
sh-2.05b$ dig @192.168.1.1 www.linuxquestions.org
; <<>> DiG 9.2.2 <<>> @192.168.1.1 www.linuxquestions.org
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28312
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 0
Sunday, November 8, 2009
Linux Servers configuration: (Squid Server)
After hearing the word "SQUID” Are you thinking about a marine creature with a distinct head, having eight arms and two longer tentacles arranged in pairs?
Nope I’m not talking about that Squid :)
Squid is a full-featured web proxy cache server application which provides proxy and cache services for Hyper Text Transport Protocol (HTTP), File Transfer Protocol (FTP), and other popular network protocols. Squid can implement caching and proxying of Secure Sockets Layer (SSL) requests and caching of Domain Name Server (DNS) lookups, and perform transparent caching. Squid also supports a wide variety of caching protocols, such as Internet Cache Protocol, (ICP) the Hyper Text Caching Protocol, (HTCP) the Cache Array Routing Protocol (CARP), and the Web Cache Coordination Protocol. (WCCP).
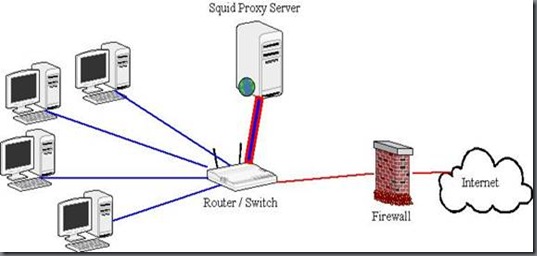
Figure Showing squid server layout.
My Experimentation Setup Layout.
Figure Showing Squid-Hierarchy-Schema.
#SQUID CONFIGURATION
NOTE: In this case 192.168.8.x is a squid server, port is 8080 in order to share internet throughout the network.
Requirements:
1) One host station.
2) One free port.
3) Package squid.
Task 1: Setup a Squid proxy server.
Step1: install package
# yum install -y squid
Step2: edit main configuration file
# vim /etc/squid/squid.conf
#(line 73) http_port 8080
Step3: service start
# service squid restart
# chkconfig squid on
Step4: go to url for checkup
#URL->edit->preference->general->connection settings->manual proxy->
http proxy-> 192.168.8.x port-> 8080
Step5: check yahoo.com first it will be blocked by stationX which u can conform from down line
Check for server1 it will come.
Task 2: INSERTING RULES:
Go to configuration file & search for INSERT (line 2517). Write down rules according to ur requirement. Few cases are here, for more cases go through file, u can give any ACL name & can deny-allow by ip/hostname.
Step1: To deny one site
#acl block url_regex .yahoo.com
#http_access deny block
Step2: To allow one network
#acl ournetworks src 192.168.8.0/24
#http_access allow ournetworks
Step3: To deny by time
#acl mytime time SMTWHFA 10:00-20:00
#http_access deny mytime
Step4: To deny one site by time
#acl block url_regex .google.com
#acl mytime time SMTWHFA 10:00-20:00
#http_access deny block mytime
Step5: Start service
# service squid restart
Step6: Go to url check for yahoo.com. It will show u access denied from 192.168.8.X, you can find it in last line and all other sites will be blocked by server1.
Task 3: Setting up "Child Proxy"
In order to make 192.168.8.x as child proxy we need one parent, here server1 is my parent and 3128 is parent proxy port.
Step1: Go to file & search for cache_peer(304 line) & edit like following
# cache_peer server1.example.com parent 3128 3130 default
Step2: start service
# service squid restart
Step3: Go to url & check.
check for yahoo.com it will be blocked & other sites will be accessed.
NOTE: For Exploring more on the acl options refer to the site: http://www.visolve.com/squid/squid24s1/access_controls.php
In case of any problem or queries or suggestions feel free to leave a comment here.. :)